Security
Users are responsible for maintaining and monitoring the usage of their own API key(s). The following
document is provided as an illustration of areas developers may wish to consider and should not be
considered formal guidance. Majestic does not offer security consultancy to end users or third party
developers.
Key security at the transport level
To ensure legacy compatibility and provide a wide range of options, the Majestic API supports several access methods.
We advise developers to check the possible risks of each access method and determine the most appropriate method for their needs.
HTTP/HTTPS
Majestic supports endpoints via both HTTP and HTTPS. The risks associated with sending requests without
transport layer security are well documented. Many modern programming languages support both HTTP and
HTTPS with very little overhead in terms of developer time. HTTP is supported for legacy reasons and
should be considered deprecated.
POST/GET
Majestic supports both POST and GET request methods for API calls.
HTTPS POST removes the need to pass parameters in the URL, reducing the opportunity
for interception.
HTTPS GET should not be considered to offer the same level of security as HTTPS POST. Whilst many
developers use GET requests when debugging or investigating aspects of web based APIs, it should be
noted that some browser plugins have sent the URLs entered to third party servers, where such data
may be made publically available via Web traffic reporting services.
As developer use of GET is considered a common use case, the Majestic API supports the passing of
app_api_key as a cookie in order to avoid the need to pass this sensitive data where it may be
intercepted. To limit potential for confusion, cookie based authentication is only supported for
HTTP(S) GET, and only when the app_api_key is not passed as a URL parameter.
Managing Key Security in the dashboard
API keys are only as secure as the context in which they are used. Providing members of staff with access to
API keys creates the possibility of malicious or accidental compromise, which needs to be considered as part
of a wider security strategy. It is therefore important for API key users to monitor the usage of the API
and to consider appropriate key management strategies.
Generating and disabling keys
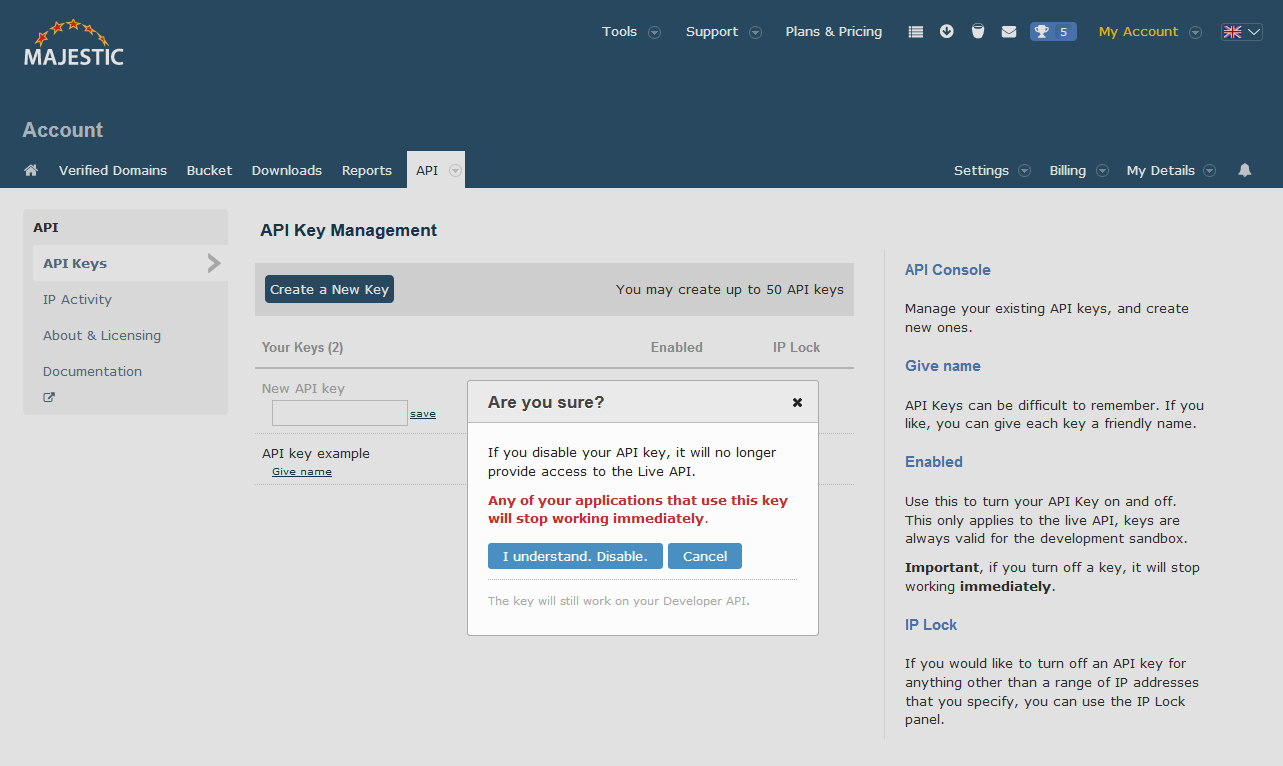
The API Key Management page is the hub for Majestic API management.
The Majestic API supports multiple keys, which may help support a key management process such as providing one key for development and another for a live environment, or potentially to re-issue keys when developers leave your organisation.
It is possible to enable or disable access on individual keys simultaneously, facilitating higher availability during product release or upgrade.
Limiting IP access
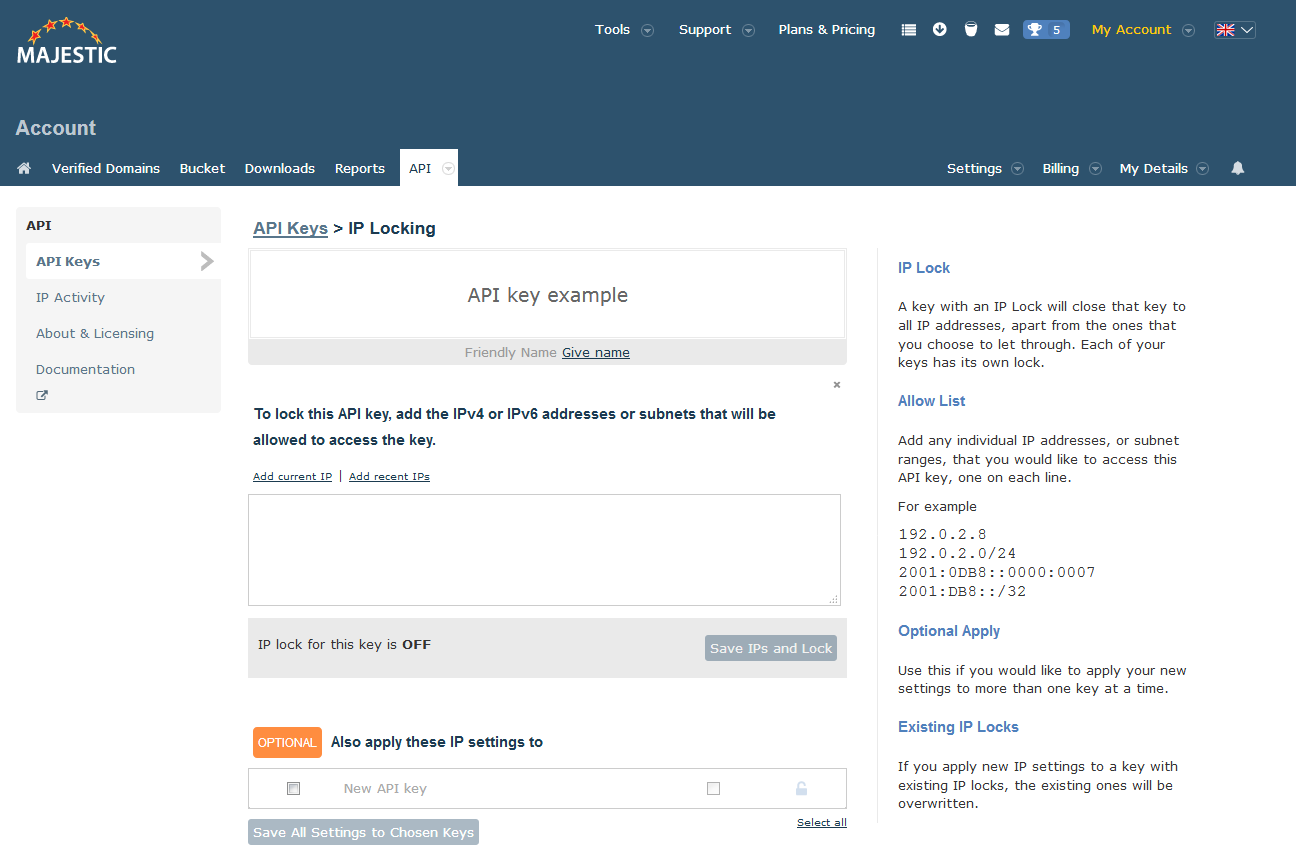
The Majestic API supports the limiting of API access to a number or range of IP addresses on a per key basis. Whitelisted IPs may be expressed
as individual IPv4 Addresses or listed together in CIDR notation (e.g 192.168.100.14/24). A white list policy may
contain a combination of IP addresses and/or CIDR notation ranges. An absence of any whitelisted addresses will cause the API key to be open to
access from all IP addresses.
Monitoring Usage
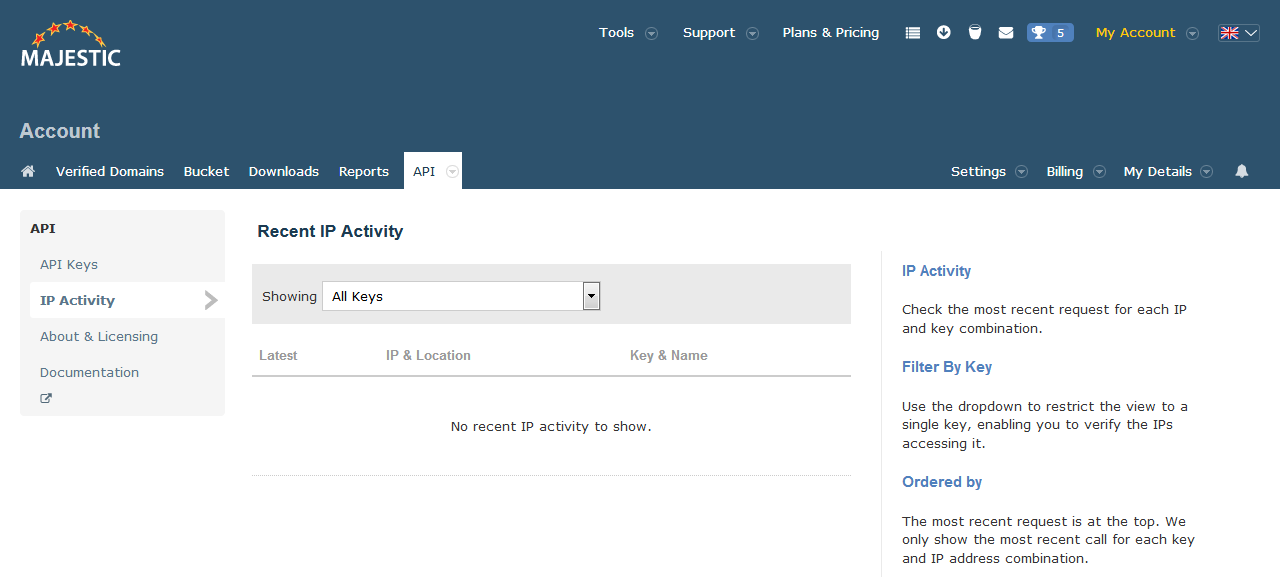
The API command GetSubscriptionInfo and the My Subscriptions page provide headline resource usage statistics.
In addition, the IP activity page in the API Management console provides a more detailed view of API usage on a key and IP address basis.



